Context-rich Cloud Security
Customer Challenges
Many cloud security solutions operate in isolation and without collective context, providing attackers with an advantage when seeking exploitable points of weakness in customer cloud environments. These technology silos result in alert fatigue, inefficiencies within teams and low ROI against expectations.
Plerion Solution
In response to these challenges, Plerion provides an all-in-one Cloud Protection Platform, that supports workloads across AWS, Microsoft Azure & GCP, delivering:
-
Cloud Security Posture Management (CSPM)
-
Cloud Workload Protection Platform (CWPP)
-
Cloud Infrastructure Entitlement Management (CIEM)
-
Attack Path Analysis
-
Software Bill of Materials (SBOM)
-
Cloud Detection and Response (CDR)
-
Extensive compliance reporting
Customer Benefits
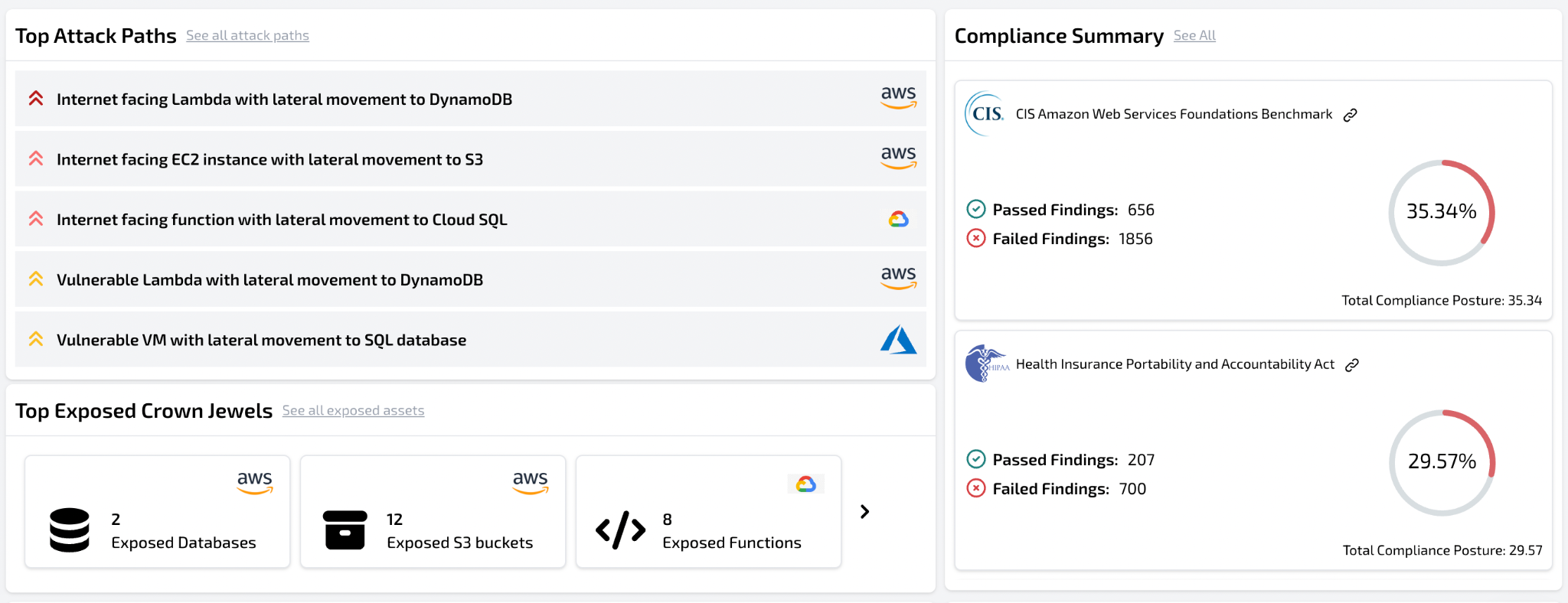
Plerion's customers can focus on the highest risk, and most impactful alerts, due to our ability to assess the key domains of Configuration, Vulnerability Management and Identity. This allows them to have a fully contextualized narrative around each finding. As a result customers are able to simplify their technology stack, reduce cost, reduce risk and fully optimize their resources.
The platform is fully aligned to a number of Compliance Standards, including Center for Internet Security (CIS),Cloud Security Alliance (CSA), Health Insurance Portability and Accountability Act (HIPAA), and many more to help teams measure and improve their compliance posture over time.
A high level overview of the highest priority items are shown in the main dashboard below.
Watch the Home Screen overview video
Plerion Security Lake
Plerion customers also have the opportunity to leverage our open data-ecosystem security lake, which provides continuous visibility of cloud resources, users, privileges and activity across cloud environments.
By leveraging Plerion's Cloud Detection and Response platform, security teams can mitigate risk early as well as investigating and responding to threats such as suspicious user activity, account compromise and malicious insider activity. Security professionals and SOC teams can leverage the consolidated data stream to uncover new threats or indicators of compromise.
End to end view of assets
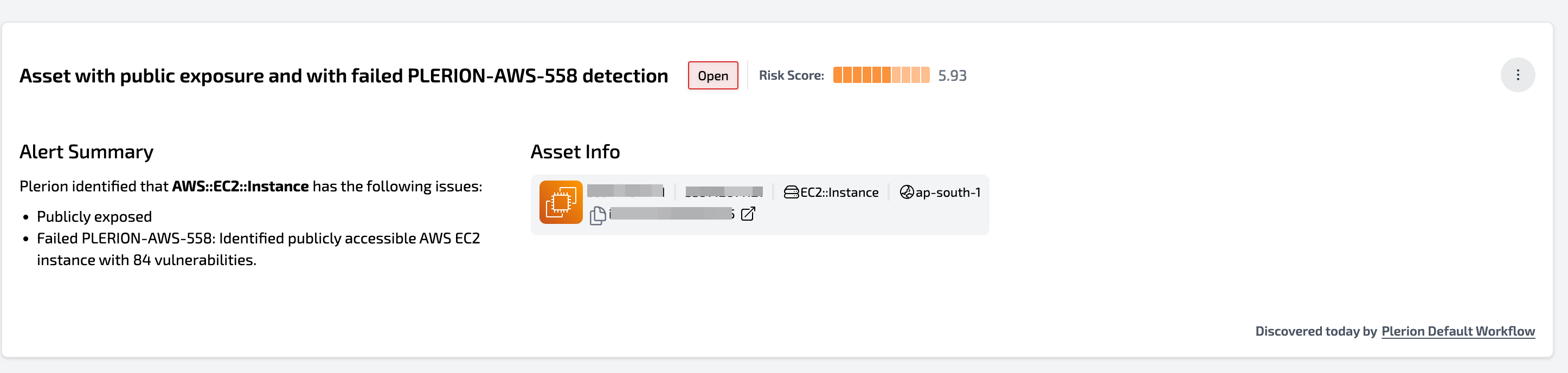
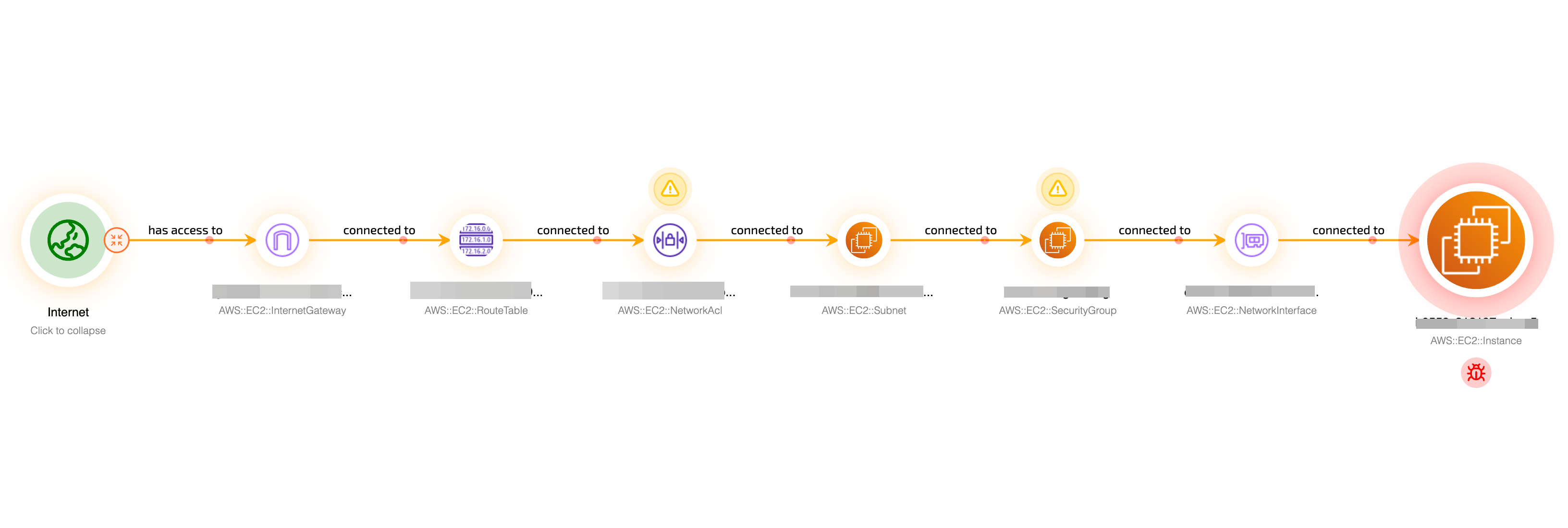
The Plerion Platform allows you the potential to understand your risk profile down to an individual asset basis. Collating data across Configuration, Identity and Vulnerability Management - all agentless - empowers customers to prioritize the risks that really matter based on impact and likelihood rather than just best practice.
Understand how a particular asset fits into an Attack Path, how to improve your position against the MITRE framework or get full details on the SBOM in order to make impactful decisions.
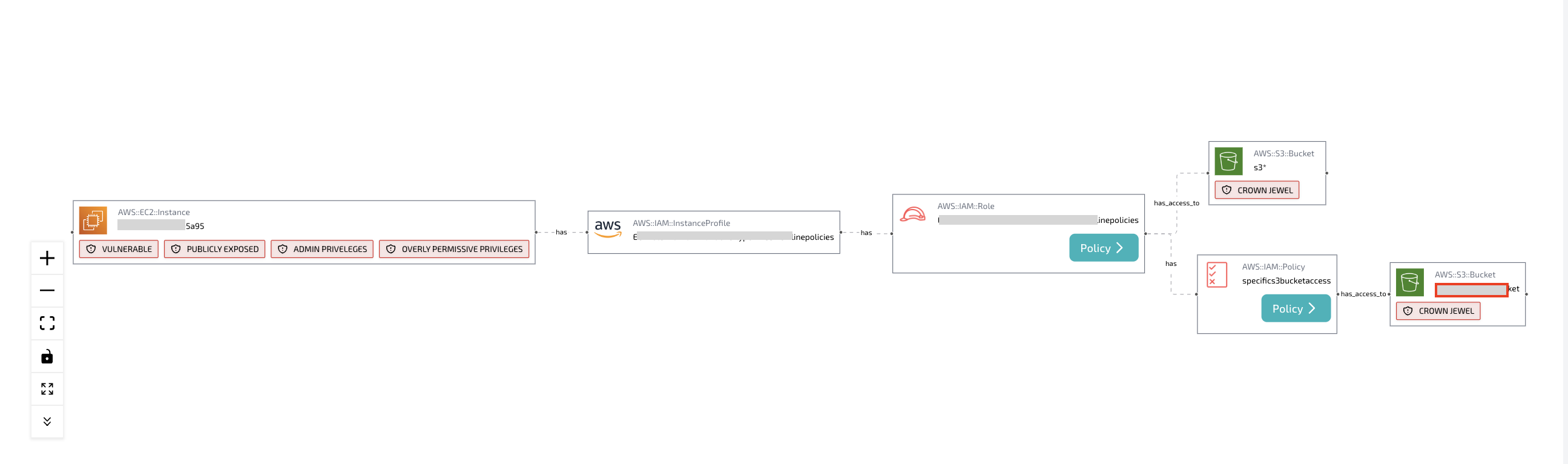
Alerts with Attack Path